On June 28, 2025, KubeEdge released v1.21.
1.21 What's New
- New Generation Node Task API and Implementation
- Support Closed Loop Flow Control
- Support Update Edge Configuration from Cloud
- Support One-Click Deployment of Dashboard and Integration of kubeedge/keink
Release Highlights
New Generation Node Task API and Implementation
In v1.21, we redesigned the status structure and operation process of node jobs to track error information and facilitate developers' understanding. In the new design, the node job status includes Phase (Init, InProgress, Completed, Failure) and nodeStatus. The nodeStatus consists of Phase (Pending, InProgress, Successful, Failure, Unknown), actionFlow, nodeName, reason, and business-related fields. A YAML example of the NodeUpgradeJob status is provided below.
status:
nodeStatus:
- actionFlow:
- action: Check
status: 'True'
time: '2025-05-28T08:12:01Z'
- action: WaitingConfirmation
status: 'True'
time: '2025-05-28T08:12:01Z'
- action: Backup
status: 'True'
time: '2025-05-28T08:12:01Z'
- action: Upgrade
status: 'True'
time: '2025-05-28T08:13:02Z'
currentVersion: v1.21.0
historicVersion: v1.20.0
nodeName: ubuntu
phase: Successful
phase: Completed
Refer to the link for more details.(#6082, #6084)
Support Closed Loop Flow Control
In v1.21, we have optimized the traffic closed-loop function of node groups. Applications within a node group can only access application services within the same group and unable to access services of other node groups. With this mechanism, users can easily achieve network isolation between multiple edge regions, ensuring that application services in different regions do not interfere with each other.
Refer to the link for more details.(#6097, #6077)
Support Update Edge Configuration from Cloud
In many cases, cloud-based direct updates to EdgeCore configuration files for edge nodes offer greater convenience than manual updates from edge node, especially for batch operations that boost efficiency by managing multiple nodes simultaneously.
In v1.21.0, ConfigUpdateJob CRD is introduced to allows users to update configuration files for edge nodes in the cloud. The updateFields within the CRD is used to specify the configuration items that need to be updated.
CRD Sample:
apiVersion: operations.kubeedge.io/v1alpha2
kind: ConfigUpdateJob
metadata:
name: configupdate-test
spec:
failureTolerate: "0.3"
concurrency: 1
timeoutSeconds: 180
updateFields:
modules.edgeStream.enable: "true"
labelSelector:
matchLabels:
"node-role.kubernetes.io/edge": ""
node-role.kubernetes.io/agent: ""
- This feature is disabled by default in v1.21.0. To enable it, please start the ControllerManager and TaskManager at cloud, as well as the TaskManager edge.
- Updating edge configurations will require a restart of EdgeCore.
Refer to the link for more details.(#6338)
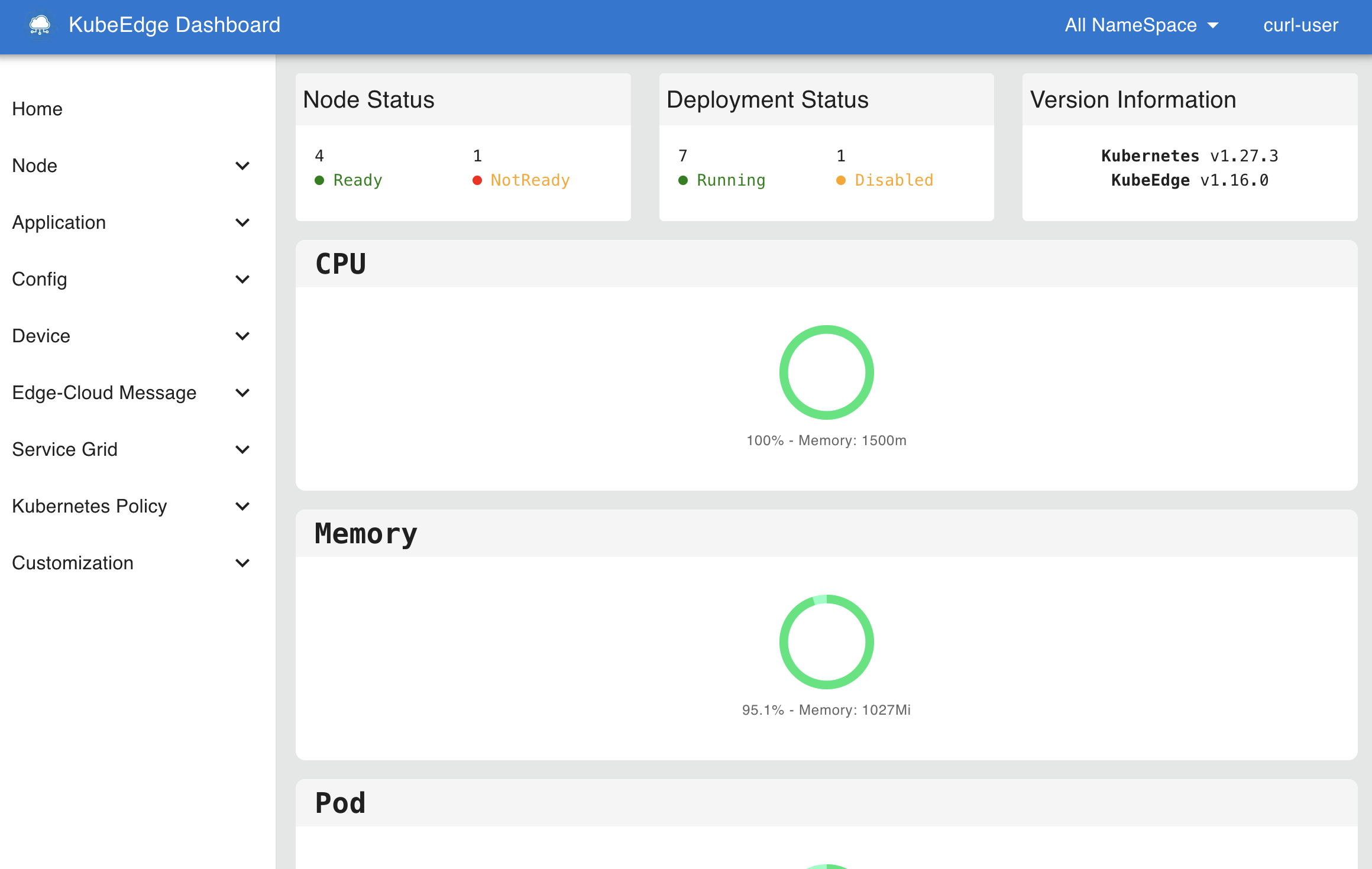
Support One-Click Deployment of Dashboard and Integration of kubeedge/keink
In v1.21, the dashboard functionality has been enhanced by designing a BFF (Backend for Frontend) layer to connect the frontend user interface layer with the KubeEdge backend API. Additionally, the dashboard is integrated with the keink project, allowing users to launch a keink cluster in the dashboard environment with just one command to experience KubeEdge features.

Refer to the link for more details.(#50)
Important Steps before Upgrading
- From v1.21, the v1alpha2 node job enables by default, and the CRD definition will be backward compatible. If you want to continue to use the v1alpha1 version of the NodeUpgradeJob and ImagePrePullJob, please setting the feature gates of ControllerManager and CloudCore.
- Add a command arg for ControllerManager:
--feature-gates=disableNodeTaskV1alpha2 - Modify the CloudCore configuration:
apiVersion: cloudcore.config.kubeedge.io/v1alpha2
kind: CloudCore
featureGates:
disableNodeTaskV1alpha2: true
...
- Add a command arg for ControllerManager:
The node job v1alpha2 CRDs are compatible with v1alpha1, but they cannot be switched between them. The code logic of v1alpha1 will destroy the data of v1alpha2 node job CR.
The v1alpha1 node jobs will no longer be maintained, and relevant codes will be clean up after v1.23. In addition, the node job has become a default disabled Beehive module in EdgeCore. If you want to use the node jobs, please modify the edgecore.yaml to enable it.
modules:
...
taskManager:
enable: true
- From v1.21, keadm upgrade related commands(backup, upgrade, rollback) at the edge have been adjusted.
- The upgrade command will not automatically execute the backup. The backup command needs to be triggered manually.
- The upgrade command hides business-related flags and relevant codes will be cleaned up after v1.23.
- All upgrade related commands use level 3 commands:
keadm edge upgrade
keadm edge backup
keadm edge rollback